
Digital Identity means to be digital-alive
Imagine the world of interconnected smart or not that smart objects exchanging all kind of information using cryptic structures, protocols and channels, pretending doing the universe a better place to live. Similar to humans, digital entities also try to find some number of attributes which would identify them among others. Having identity means to be alive.Of course, there is an ISO definition for Digital Identity. According to ISO/IEC 24760–1 Digital Identity means:
For the purpose of this article, we can understand Digital Identity as a (unique) identification of a real life subject (person) within specific digital platform, reflection of human person in the world of zeros and ones.
No Win-Win, no fun, no business
The primary goal why the companies interact with people on a digital platform is to generate revenue. Simple as that. In the first step, they need to somehow attract consumers. Yes, they prefer to call this enforcement attraction. “I need you, because I need your money” has to be translated in favor of potential consumers, so companies come up with win-win model or at least pretend to have it.
D: If you consume my service, I will give you some benefit, maybe goods. I: Okay, I feel I may need your service, may I come to you? D: Of course, please follow this link and register to my platform. You will get extra -10% on your next order. Do you know it? This is, where digital relationship starts, this is, where you earn recognition as Digital Identity within specific platform. Now, both parties are happy, you get access to the new world, on the dashboard of marketing director blinks “You are doing well, the number of converted anonymous visitors into recognized consumers has been increased.”The rise of Digital Identity Fraud

Identity may incorporate set of privileges gained upon time by various certifications and attestations. Stealing human identity verified by ID Card, Passport or Credit Card is a gateway for attacker to services which is the victim eligible for. In the digital world, gaining access to verified digital account impose risk of unauthorized service consumption by the attacker. Credit Cards, Loans, Legal and Government Documents, Company Assets are the examples of attack objectives.
NumbersAccording to the PWC’s Global Economic Crime and Fraud Survey for 2020 47% of responding companies faced a fraud incident within last 24 months on average six cases. Identity fraud, representing 35% of all fraud crimes was the leading crime. The cumulative financial loss of the global economy represents $5tn, with the 15% increase in 2020.
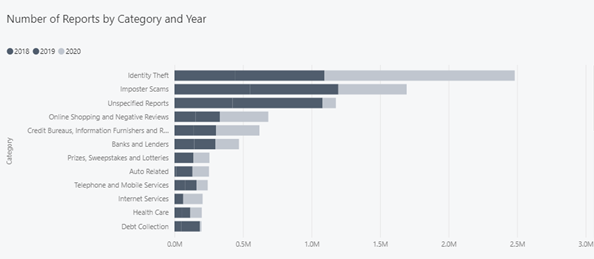
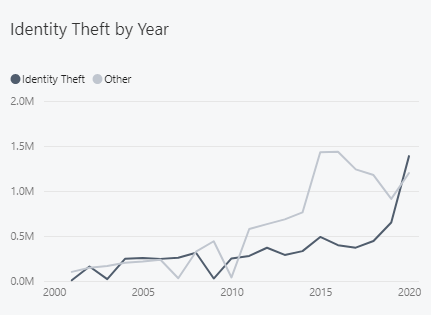
Federal Trade Commission reported the raise of Identity Theft by alarming 213% between years 2019–2020 (dataset). The Identity Theft represents the major category in cyber crimes. The pandemics age forced many companies to quick transformation to digital services which increased the attack surface. To be honest, many service providers did it wrong, they just impose some online service and will invest into security after first significant attack occurs. They will probably not discover it, just receive the information from local media, where the consumers have complained about it.
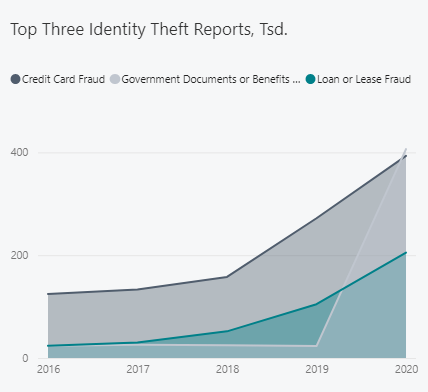
Financial benefits are the most common target of the Identity Frauds. Credit Cards and Loan Frauds are in the top three Identity Theft reports. The misuse of Digital Identity regarding credit cards is not only related to the banks and financial institutions, the majority comes from other use cases where credit cards are involved — subscriptions, e-shops, other online services. If you just find some unbelievable price drop advertisement on social media and you enter your credit card details into unsecure payment gateway, you are probably already in trouble. The median loss per fraud reports is $311 (dataset).
Security analysts reported attack vector has been moved over years from short-time — penetration- gaining as much as possible-disappearance — to long time presence of the attacker within compromised platform. To enable such kind of presence, attacker need to be covered by digital identity, which basically behaves similar to common consumer. Higher intelligence costs compromising digital identity are rewarded by long term benefits for attacker. New Account Creation and Account Take Over are the attack vectors with highest incidence.
I will impersonate you!
Imagine following situation: you want to buy a new car, you enter the bank, identify yourself and ask for credit/loan/lease options. After a while the bank representative turns to you with well trained poker face. You were told you are not eligible to get any money, your risk score is to high because of multiple smaller loans from the short past. You didn’t ask for credit for several years neither in the bank nor using online banking app as seen in advertisements, you even don’t have account there.
The fact, you don’t have online banking account means your digital trace within underlying bank does not exist or in very limited way. Maybe you feel safe not exposing your financial behavior details, on the other side, the anomaly detection algorithms, all the behavioral analytics feel sad about you, they don’t know you, they hardly can warn the institution if somebody creates digital identity on your behalf with correct personal information. This is a very simple example of New Account Creation Identity Fraud. Relying on stolen identity data about real person, trying to convince authorities, mapping fake digital identity on attacker expose to-you-eligible services in favor somebody else.
Mule Accounts are also good example of New Account Creation Identity Fraud.
Account Takeover Fraud rely on the existing digital identity account, which probably has its own behavioral history, which makes it easier for behavioral intelligence to discover it. Of course, if proper analytics engine has been set up. In terms of complexity, it is easier for attacker to steal or buy compromised customer logins in comparison to New Account Creation, where the attacker need to convince verification authority proving that digital identity account is owned by subject the identity attributes are related to. Takeover frauds are mostly used in financial sector — banks, financial accounts, pensions, insurance, medical accounts, real estate, rewards programs. Other than financial fraud, the COVID-19 pandemics shed light on the industry know-how frauds, where the hackers steal the patents, procedures plans or other company secured assets.
By the end of 2020, the Federal Trade Commission reported more than $3,3 bn. financial loss cumulated in digital world. Identity Theft represents almost 30% of the total number. The median loss represents $311 per fraud (dataset).
Security inspired trust relationship
Some people use to find trust necessary if the knowledge is missing, or it cannot be gathered in a meaningful amount of time and energy. The average consumer of your services has no chance to verify your platform is secure, so without obvious security issues, he/she will tend to trust your system. So far so good. If your services offer primary or secondary financial benefits you can be sure, soon or later, you are on attackers’ radar. And even single Account Takeover with average financial loss can destroy over years built good will among your customers. One negative experience will become more attractive as 100K satisfied customers.
360° security model together with recommendations will be described in the next part. One of the biggest challenge is to balance Security with User Experience.
Please, prove your Identity!
Identity Proving aims to verify the link between virtual Digital Identity and physical subject claiming its ownership.
Risk:This risk is very simple and just to high to ignore it. It could be just anything/anybody behind unproved digital identity. There are of course scenarios, when the Identity Verification does not play a crucial role. The very simple reseller eshop requires you to put your delivery and payment data, but your identity does not play any special role here. After payment, goods are delivered to customer or returned back to reseller.
Do it on regular basis, even randomly. Motivate consumers with extra benefits for proving their identity. It is still better to know your customers even not necessary, your analytics will be grateful for that.
Foto/Video chat: could be understood as a virtual alternative for onsite verification in office, where human identity is being verified against ID document. Some selected Identity Verification Provider (DACH region): (youniqx.com, verify-u.de, idnow.io, webid-solutions.de, deutschepost.de).
Online Banking: This process rely on premise, your bank or other financial institution has already proved your identity and this trust is bridged to the other service, the identity holder wants to consume.
ID documents verification: Real-time/offline verification of scanned ID documents. Artificial Intelligence often takes place for image and text recognition, document validation and computing the lexical difference to the data stored in your digital identity profile.
Trusted e-Government Solution: Similar to the online banking, you can use the trusted government services to verify consumer’s digital identity. Such a trust chain is very popular and relatively easy to implement, as you just need to connect with existing solution over provided interface. Probably some SSL certificates will be required to enable trusted connection between your service and the Identity Provider/Verifier service. Some examples of such a government solutions are: eIDAS, Handy Signatur AT, ID Austria.
iloveyou 123456 P@ssword and other Intelligence

Risk:
Password misuse leads to various types of Account Takeovers. The holder of digital identity is no longer a single subject. Compromised passwords are often publicly available — for not so little amount of time, anybody with internet connection can access these accounts and try to gain some benefit out of them.
Implement proper Password Intelligence using the password policies. According to OWASP, some essential rules for passwords are required:
- Minimal length > 8 characters (NIST SP800–63B)
- Maximum length < 64, due to limitations in certain hashing algorithms
- All characters including unicode and whitespaces are allowed, no password composition rules limiting the type of characters are permitted
- Use password strength helper to help users create a more secure password, block common and previously breached passwords — there are already services to check against compromised passwords (Pwned Passwords)
- One-Time/Initial Passwords have to be random
- The application should not keep a password history and force users to periodic password rotation
- Digital Identity Guidelines, Authentication and Lifecycle Management NIST SP800–63B
- OWASP Authentication Cheat Sheet
- Breached Passwords API
- Password strength estimator
Wrap-up
